
Today we will talk about what it is NetDB, SusiDNS and about the initial initialization of the I2P network.
Very soon the Internet in Russia will become not free, Various providers are already blocking certain sites.
And a blocked resource has two ways:
1) Hope that the user will access the site through a proxy/VPN
2) Move the site to a decentralized, anonymous network
PS Perhaps, I can only call I2P a real decentralized and anonymous network, TOR does not fall under this definition, due to the fact that the principle of the TOR network is different - multi-level proxy access to the regular Internet, and .onion resources as a nice bonus.
In an I2P network, everything is the other way around, the main thing is internal resources and the external proxy is a bonus.
How the initial initialization of an I2P network occurs?
After downloading the distribution and installing it, the I2P network tries to initialize, searching for local nodes By NetDB (DHT) if no nodes are found, the initial list of nodes is requested by
specific http(s) addresses.
An interesting feature: nodes that are obtained during initial initialization cannot be final when accessing internal sites. (This is done in order to eliminate the possibility of the government creating nodes and analyzing traffic) if the node is created by a malicious group of people, then it will still only transmit anonymous traffic to another node, no more.
After receiving the first addresses of I2P network participants via a standard https connection, the client tries to connect to them and NetDB starts.
What is NetDB?
The simplest definition of NetDB technology is like DHT in the Torrent protocol.
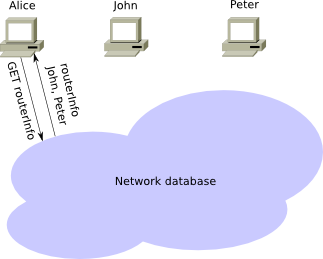
NetDB is a distributed database of network participants, it is through it that access tunnels to sites are configured, but what is interesting is that your personal ID is not sent to the network, so it is impossible to make an analogy between IP and I2P ID.
Of course, NetDB also stores keys that indicate the authenticity of the information published there.

What else is stored there??
— Node tunnel installation statistics
— Number of successfully established connections through the node
— Number of dropped connections
— Timeout time when accessing a node
— Router version (I2P client)
The NetDB network supports all the same peer ban functions as the DHT network in the torrent protocol (for example, if the router’s ratio of successfully completed connections to connections with errors is too high)
Thus, once you have established a connection to NetDB, you will always have access to the I2P network in the future.
And on a special website - stats.i2p you can see the current state of the network, which is determined through NetDB:

Floodfill routers are those routers that have a fully up-to-date NetDB database or close to up-to-date
What is SusiDNS?

Resources on the I2P network have their own top-level domain - .I2P
But since there are no IP addresses in I2P, the DNS service there is special.
Essentially, DNS in I2P is a huge hosts file.
Initially, the distribution is able to obtain the I2P host: internal ID ratio only from the native registrar, but there are many registrars on the network that allow you to register your site, no matter what it is and no matter what you write about on it.
The most popular — http://inr.I2P
But you don’t have to subscribe to domain registrars; you can save the match for each name yourself.
Using jump services or entering a long hash of the host address.
Thus, at this stage the network is fighting cyberstuttering.
But in any case, when the network gains popularity, there will most likely be 1 registrar (or no more than 3, the most popular) and it is for registration that they will (pay money?) fight.
It is also possible to use the Namecoin service in place of the existing DNS network in I2P; at the present time, active developments are underway in this direction.
Official project website: http://i2p2.de
What else to read about I2P:
Preparing for the onset of the Great Russian Firewall
I2P - Creating your own website
I2P – Invisible Internet Project